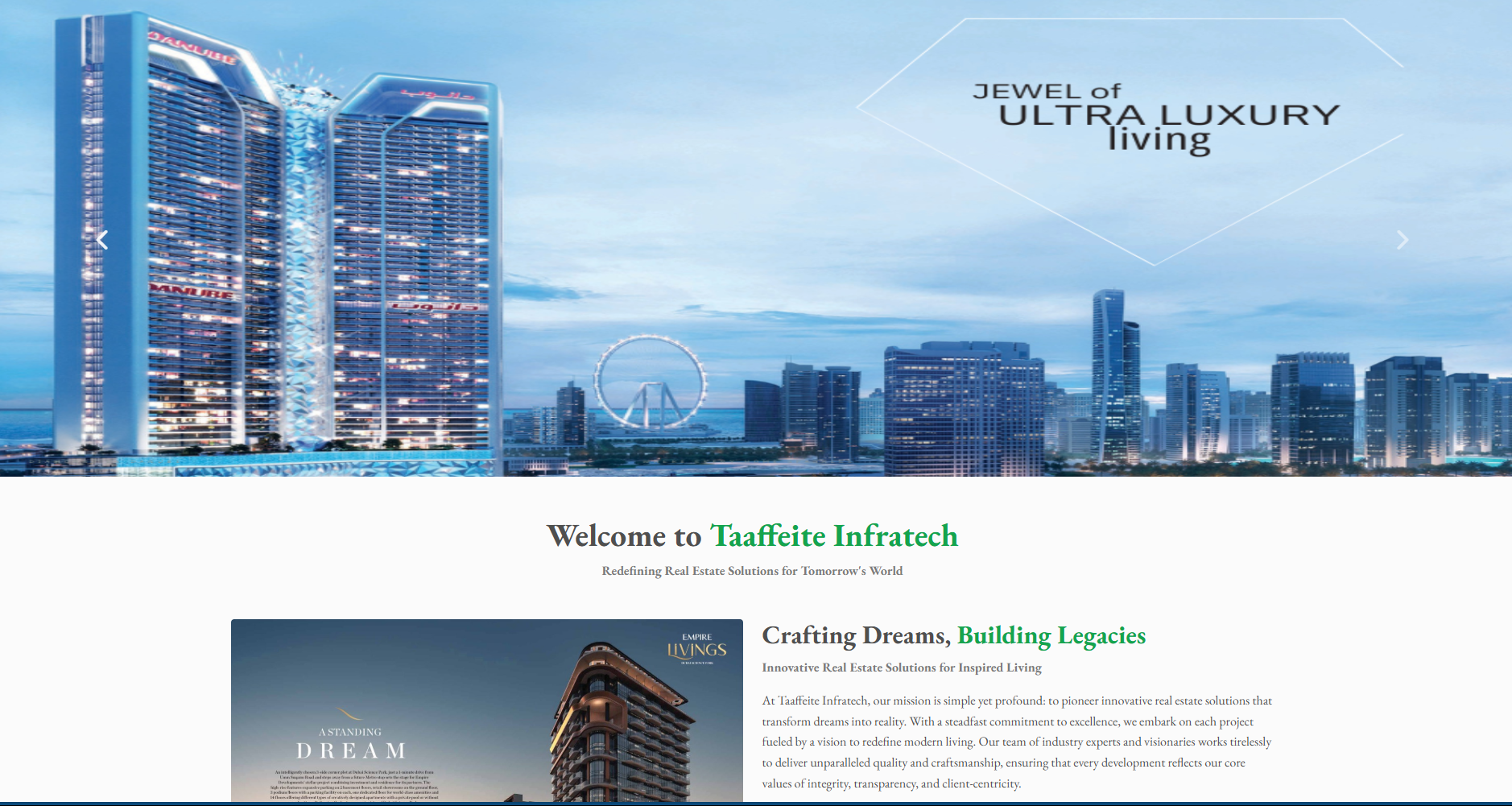
Comprehensive Cyber Security
Protect your software and applications from malicious with our security services
Our Services
Comprehensive solutions to protect your business from digital threats.
Threat Detection
Identify vulnerabilities and protect your systems in real-time.
Access Management
Secure authentication systems for robust data protection..
Network Security
Advanced firewalls and intrusion prevention systems.
Vulnerability Assessment
Comprehensive security checks to prevent breaches.
Data Encryption
Robust backend systems for secure and scalable apps.
Cloud Security
Ensure the safety of cloud-based applications and data.
Our Key Benefits
Comprehensive Protection
Protect your organization from a wide range of threats including malware, ransomware, and phishing.
Identity Protection
Secure personal and corporate identities from unauthorized access and cyber theft.
Network Security
Advanced network protection strategies to prevent cyber-attacks and unauthorized access.
Data Encryption
End-to-end encryption to safeguard sensitive data from interception and tampering.
Business Continuity
Ensure your business stays operational with disaster recovery plans and backup strategies.
Continuous Monitoring
24/7 monitoring and real-time alerts to detect potential vulnerabilities before they cause harm.
Our Features
Explore the advanced features that protect your organization’s digital assets.
Advanced Threat Protection
Detect and block advanced malware, ransomware, and other cyber threats in real-time.
Identity & Access Management
Control and manage user access to critical systems to prevent unauthorized access.
Network Security
Safeguard your network from intrusions and cyber-attacks using the latest security protocols.
Data Encryption
Ensure all sensitive data is encrypted both at rest and in transit to prevent interception.
Automated Incident Response
Automate responses to cyber incidents to minimize the impact of threats on your business.
Cloud Security
Protect your cloud infrastructure with advanced security measures and ensure safe data storage.
Our Cybersecurity Process
Follow our comprehensive process to ensure your business stays protected from digital threats.
Our Projects
Explore some of the best work we've done for our clients.

Project 1
Description of the project goes here.

Project 2
Description of the project goes here.

Project 3
Description of the project goes here.
Testimonials
What our clients are saying about us